A security analyst has determined the security team should take action based on the following log:
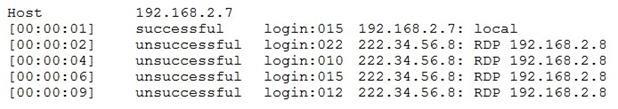

Which of the following should be used to improve the security posture of the system?
A. Enable login account auditing.
B. Limit the number of unsuccessful login attempts.
C. Upgrade the firewalls.
D. Increase password complexity requirements.
