A security analyst is monitoring authentication exchanges over the company’s wireless network. A sample of the Wireshark output is shown below:
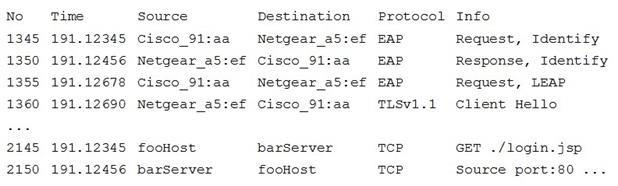

Which of the following would improve the security posture of the wireless network?
A. Using PEAP instead of LEAP
B. Using SSL 2.0 instead of TLSv1.1
C. using aspx instead of .jsp
D. Using UDP instead of TCP
