While investigating suspicious activity on a server, a security administrator runs the following report:
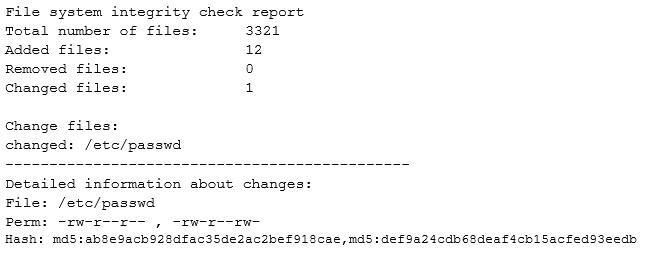

In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describes this scenario? (Choose two.)
A. An attacker compromised the server and may have used a collision hash in the MD5 algorithm to hide the changes to the /etc/shadow file
B. An attacker compromised the server and may have also compromised the file integrity database to hide the changes to the /etc/shadow file
C. An attacker compromised the server and may have installed a rootkit to always generate valid MD5 hashes to hide the changes to the /etc/shadow file
D. An attacker compromised the server and may have used MD5 collision hashes to generate valid passwords, allowing further access to administrator accounts on the server
E. An attacker compromised the server and may have used SELinux mandatory access controls to hide the changes to the /etc/shadow file
Correct Answer: AD
