A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices.
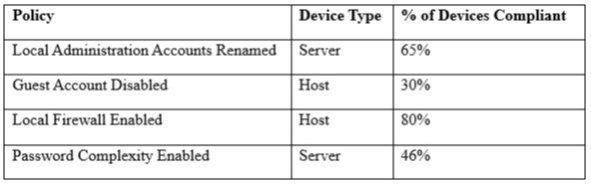

Which of the following tools is the security engineer using to produce the above output?
A. Vulnerability scanner
B. SIEM
C. Port scanner
D. SCAP scanner
Correct Answer: B
