A security professional is analyzing the results of a network utilization report. The report includes the following information:
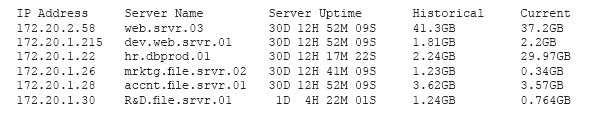

Which of the following servers needs further investigation?
A. hr.dbprod.01
B. R&D.file.srvr.01
C. mrktg.file.srvr.02
D. web.srvr.03
