An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security analyst is reviewing vulnerability scan results from a recent web server scan. Portions of the scan results are shown below:
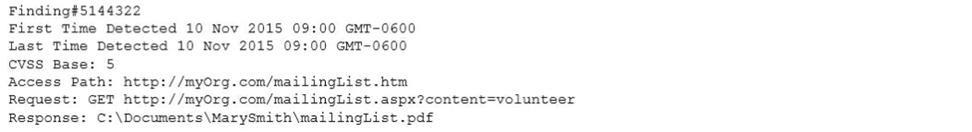

A. Response: C:\Documents\MarySmith\mailingList.pdf
B. Finding#5144322
C. First Time Detected 10 Nov 201 5 09:00 GMT-0600
D. Access Path: http://myOrg.com/mailingListhtm
E. Request: GEThttp://myOrg,com/mailingList.aspx?content=volunteer
