When reviewing network traffic, a security analyst detects suspicious activity:
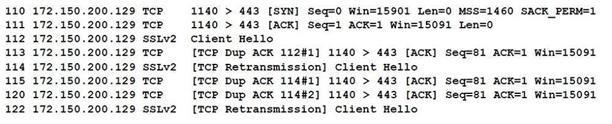

Based on the log above, which of the following vulnerability attacks is occurring?
A. ShellShock
B. DROWN
C. Zeus
D. Heartbleed
E. POODLE
When reviewing network traffic, a security analyst detects suspicious activity:


Based on the log above, which of the following vulnerability attacks is occurring?
A. ShellShock
B. DROWN
C. Zeus
D. Heartbleed
E. POODLE