Given the following access log:
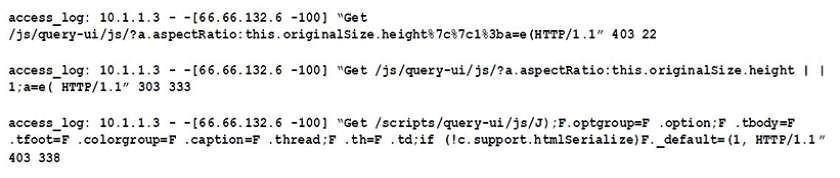

Which of the following accurately describes what this log displays?
A. A vulnerability in jQuery
B. Application integration with an externally hosted database
C. A vulnerability scan performed from the Internet
D. A vulnerability in Javascript
