Company A’s security policy states that only PKI authentication should be used for all SSH accounts. A security analyst from Company A is reviewing the following auth.log and configuration settings:
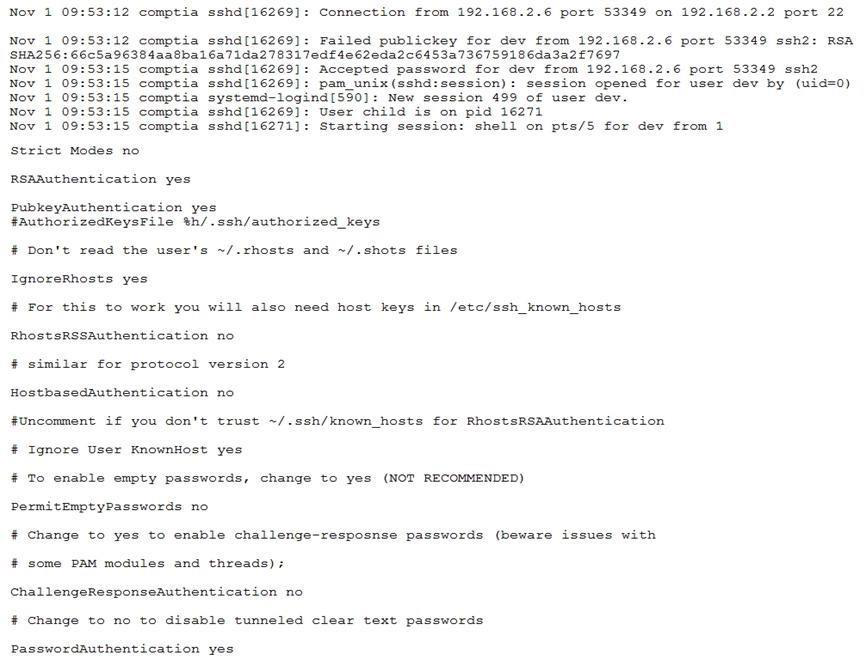

Which of the following changes should be made to the following sshd_config file to establish compliance with the policy?
A. Change PermitRootLoginno to #PermitRootLoginyes
B. Change ChallengeResponseAuthentication yes to ChallangeResponseAuthentication no
C. Change PubkeyAuthentication yes to #PubkeyAuthentication yes
D. Change #AuthorizedKeysFile sh/.ssh/authorized_keys to AuthorizedKeysFile sh/.ssh/authorized_keys
E. Change PassworAuthentication yes to PasswordAuthentication no
