A cybersecurity analyst is currently using Nessus to scan several FTP servers. Upon receiving the results of the scan, the analyst needs to further test to verify that the vulnerability found exists. The analyst uses the following snippet of code:
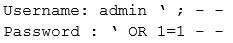

Which of the following vulnerabilities is the analyst checking for?
A. Buffer overflow
B. SQL injection
C. Default passwords
D. Format string attack
