A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?
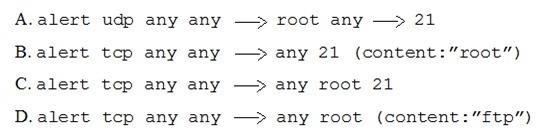

A. Option A
B. Option B
C. Option C
D. Option D
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?


A. Option A
B. Option B
C. Option C
D. Option D