After completing a vulnerability scan, the following output was noted:
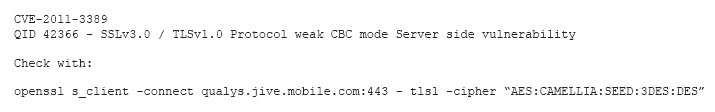

Which of the following vulnerabilities has been identified?
A. PKI transfer vulnerability.
B. Active Directory encryption vulnerability.
C. Web application cryptography vulnerability.
D. VPN tunnel vulnerability.
