A cybersecurity analyst is reviewing log data and sees the output below:
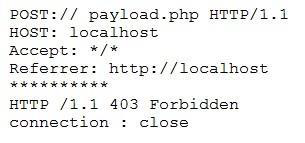

Which of the following technologies MOST likely generated this log?
A. Stateful inspection firewall
B. Network-based intrusion detection system
C. Web application firewall
D. Host-based intrusion detection system
