An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has received the following output from the latest scan:
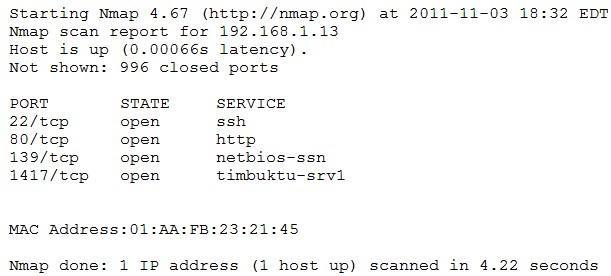

The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
A. nmap -sV 192.168.1.13 -p1417
B. nmap -sS 192.168.1.13 -p1417
C. sudo nmap -sS 192.168.1.13
D. nmap 192.168.1.13 -v
