Case study –
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study –
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.
Background –
City Power & Light company provides electrical infrastructure monitoring solutions for homes and businesses. The company is migrating solutions to Azure.
Current environment –
Architecture overview –
The company has a public website located at http://www.cpandl.com/. The site is a single-page web application that runs in Azure App Service on Linux. The website uses files stored in Azure Storage and cached in Azure Content Delivery Network (CDN) to serve static content.
API Management and Azure Function App functions are used to process and store data in Azure Database for PostgreSQL. API Management is used to broker communications to the Azure Function app functions for Logic app integration. Logic apps are used to orchestrate the data processing while Service Bus and Event Grid handle messaging and events.
The solution uses Application Insights, Azure Monitor, and Azure Key Vault.
Architecture diagram –
The company has several applications and services that support their business. The company plans to implement serverless computing where possible. The overall architecture is shown below.
User authentication –
The following steps detail the user authentication process:
- The user selects Sign in in the website.
- The browser redirects the user to the Azure Active Directory (Azure AD) sign in page.
- The user signs in.
- Azure AD redirects the user’s session back to the web application. The URL includes an access token.
- The web application calls an API and includes the access token in the authentication header. The application ID is sent as the audience (`˜aud’) claim in the access token.
- The back-end API validates the access token.
Requirements –
Corporate website –
Communications and content must be secured by using SSL.
Communications must use HTTPS.
Data must be replicated to a secondary region and three availability zones.
Data storage costs must be minimized.
Azure Database for PostgreSQL –
The database connection string is stored in Azure Key Vault with the following attributes:
- Azure Key Vault name: cpandlkeyvault
- Secret name: PostgreSQLConn
- Id: 80df3e46ffcd4f1cb187f79905e9a1e8
The connection information is updated frequently. The application must always use the latest information to connect to the database.
Azure Service Bus and Azure Event Grid
Azure Event Grid must use Azure Service Bus for queue-based load leveling.
Events in Azure Event Grid must be routed directly to Service Bus queues for use in buffering.
Events from Azure Service Bus and other Azure services must continue to be routed to Azure Event Grid for processing.
Security –
All SSL certificates and credentials must be stored in Azure Key Vault.
File access must restrict access by IP, protocol, and Azure AD rights.
All user accounts and processes must receive only those privileges which are essential to perform their intended function.
Compliance –
Auditing of the file updates and transfers must be enabled to comply with General Data Protection Regulation (GDPR). The file updates must be read-only, stored in the order in which they occurred, include only create, update, delete, and copy operations, and be retained for compliance reasons.
Issues –
Corporate website –
While testing the site, the following error message displays:
CryptographicException: The system cannot find the file specified.
Function app –
You perform local testing for the RequestUserApproval function. The following error message displays:
‘Timeout value of 00:10:00 exceeded by function: RequestUserApproval’
The same error message displays when you test the function in an Azure development environment when you run the following Kusto query:
FunctionAppLogs –
| where FunctionName = = “RequestUserApproval”
Logic app –
You test the Logic app in a development environment. The following error message displays:
‘400 Bad Request’
Troubleshooting of the error shows an HttpTrigger action to call the RequestUserApproval function.
Code –
Corporate website –
Security.cs:

Function app –
RequestUserApproval.cs:
HOTSPOT –
You need to retrieve the database connection string.
Which values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
![]()

Azure database connection string retrieve REST API vault.azure.net/secrets/
Box 1: cpandlkeyvault –
We specify the key vault, cpandlkeyvault.
Scenario: The database connection string is stored in Azure Key Vault with the following attributes:
Azure Key Vault name: cpandlkeyvault
Secret name: PostgreSQLConn –
Id: 80df3e46ffcd4f1cb187f79905e9a1e8
Box 2: PostgreSQLConn –
We specify the secret, PostgreSQLConn
Example, sample request:
https://myvault.vault.azure.net//secrets/mysecretname/4387e9f3d6e14c459867679a90fd0f79?api-version=7.1
Box 3: Environment-
Reference: https://docs.microsoft.com/en-us/rest/api/keyvault/getsecret/getsecret
Question 2.
DRAG DROP –
You need to correct the corporate website error.
Which four actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
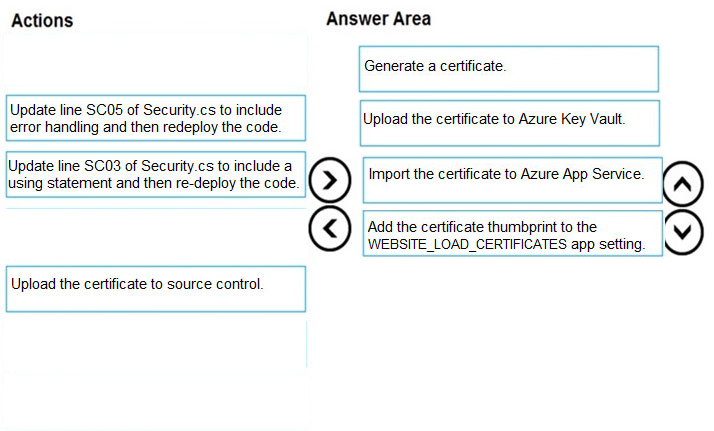
Scenario: Corporate website –
While testing the site, the following error message displays:
CryptographicException: The system cannot find the file specified.
Step 1: Generate a certificate –
Step 2: Upload the certificate to Azure Key Vault
Scenario: All SSL certificates and credentials must be stored in Azure Key Vault.
Step 3: Import the certificate to Azure App Service
Step 4: Add the certificate thumbprint to the WEBSITE_LOAD_CERTIFICATES app settings.
Reference: https://docs.microsoft.com/en-us/azure/app-service/configure-ssl-certificate
Question 3.
HOTSPOT –
You need to configure API Management for authentication.
Which policy values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:

Box 1: Validate JWT –
The validate-jwt policy enforces existence and validity of a JWT extracted from either a specified HTTP Header or a specified query parameter.
Scenario: User authentication (see step 5 below)
The following steps detail the user authentication process:
1. The user selects Sign in in the website.
2. The browser redirects the user to the Azure Active Directory (Azure AD) sign in page.
3. The user signs in.
4. Azure AD redirects the userג€™s session back to the web application. The URL includes an access token.
5. The web application calls an API and includes the access token in the authentication header. The application ID is sent as the audience (ג€˜audג€™) claim in the access token.
6. The back-end API validates the access token.
Incorrect Answers:
✑ Limit call rate by key – Prevents API usage spikes by limiting call rate, on a per key basis.
✑ Restrict caller IPs – Filters (allows/denies) calls from specific IP addresses and/or address ranges.
✑ Check HTTP header – Enforces existence and/or value of a HTTP Header.
Box 2: Inbound-
Authentication should be done on Incoming Request and that should be done in Inbound section of the policy of course.
Quoting:
This policy can be used in the following policy sections and scopes.
Policy sections: inbound
Policy scopes: all scopes
Question 4.
You need to authenticate the user to the corporate website as indicated by the architectural diagram.
Which two values should you use? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. ID token signature
B. ID token claims
C. HTTP response code
D. Azure AD endpoint URI
E. Azure AD tenant ID
Correct Answer: DE
User authentication flow-
The following steps detail the user authentication process:
1. The user selects Sign in in the website.
2. The browser redirects the user to the Azure Active Directory (Azure AD) sign in page.
3. The user signs in.
4. Azure AD redirects the user’s session back to the web application. The URL includes an access token.
To redirect user for authentication when user clicks on Sign in, we need Azure AD endpoint URI and Azure AD tenant ID.
Question 5.
HOTSPOT –
You need to correct the Azure Logic app error message.
Which configuration values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
![]()

Scenario: You test the Logic app in a development environment. The following error message displays:
‘400 Bad Request’
Troubleshooting of the error shows an HttpTrigger action to call the RequestUserApproval function.
Note: If the inbound call’s request body doesn’t match your schema, the trigger returns an HTTP 400 Bad Request error.
Box 1: anonymous-
Box 2: system-assigned –
Your logic app or individual connections can use either the system-assigned identity or a single user-assigned identity, which you can share across a group of logic apps, but not both.
Question 6
HOTSPOT –
You need to configure Azure Service Bus to Event Grid integration.
Which Azure Service Bus settings should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
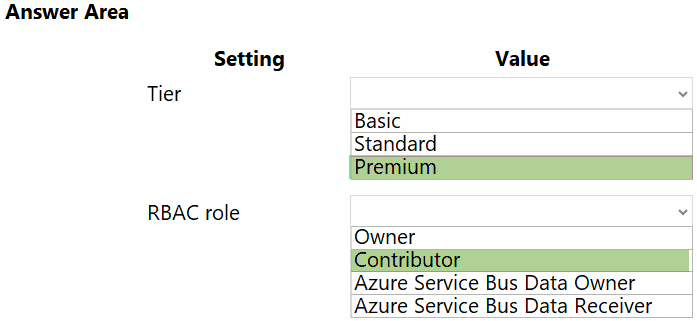
Box 1: Premium –
Service Bus can now emit events to Event Grid when there are messages in a queue or a subscription when no receivers are present. You can create Event Grid subscriptions to your Service Bus namespaces, listen to these events, and then react to the events by starting a receiver. With this feature, you can use Service
Bus in reactive programming models.
To enable the feature, you need the following items:
A Service Bus Premium namespace with at least one Service Bus queue or a Service Bus topic with at least one subscription.
Contributor access to the Service Bus namespace.
Box 2: Contributor –
Reference: https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-to-event-grid-integration-concept
Question 7.
You need to investigate the Azure Function app error message in the development environment.
A. Connect Live Metrics Stream from Application Insights to the Azure Function app and filter the metrics.
B. Create a new Azure Log Analytics workspace and instrument the Azure Function app with Application Insights.
C. Update the Azure Function app with extension methods from Microsoft.Extensions.Logging to log events by using the log instance.
D. Add a new diagnostic setting to the Azure Function app to send logs to Log Analytics.
Correct Answer: A
Azure Functions offers built-in integration with Azure Application Insights to monitor functions.
The following areas of Application Insights can be helpful when evaluating the behavior, performance, and errors in your functions:
Live Metrics: View metrics data as it’s created in near real-time.
Failures –
Performance –
Metrics –
Question 8
HOTSPOT –
You need to configure security and compliance for the corporate website files.
Which Azure Blob storage settings should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
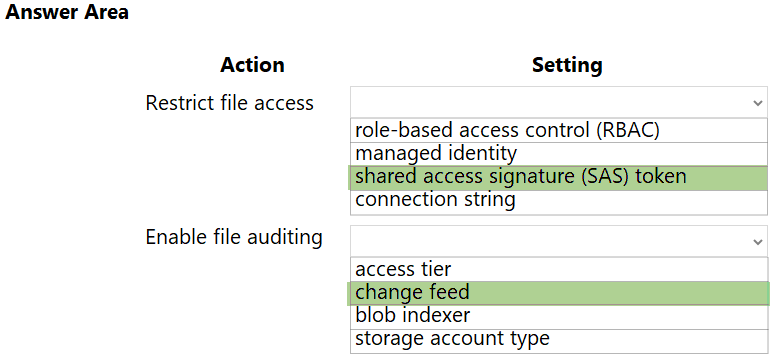
Box 1: shared access signature (SAS) token
According to the diagram, blob storage is accessed from Azure CDN. Azure CDN doesn’t support authentication with managed identity. If you want to grant limited access to private storage containers, you can use the Shared Access Signature (SAS) feature of your Azure storage account. Also, using a managed identity you can’t restrict access by IP as requested.
Box 2: change feed
The purpose of the change feed is to provide transaction logs of all the changes that occur to the blobs and the blob metadata in your storage account.
The file updates must be read-only, stored in the order in which they occurred, include only create, update, delete, and copy operations, and be retained for compliance reasons.
Reference:
https://docs.microsoft.com/en-us/azure/cdn/cdn-sas-storage-support
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-change-feed?tabs=azure-portal
