Question #44
HOTSPOT –
You need to design an Azure policy that will implement the following functionality:
✑ For new resources, assign tags and values that match the tags and values of the resource group to which the resources are deployed.
✑ For existing resources, identify whether the tags and values match the tags and values of the resource group that contains the resources.
✑ For any non-compliant resources, trigger auto-generated remediation tasks to create missing tags and values.
The solution must use the principle of least privilege.
What should you include in the design? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:


Correct Answer:
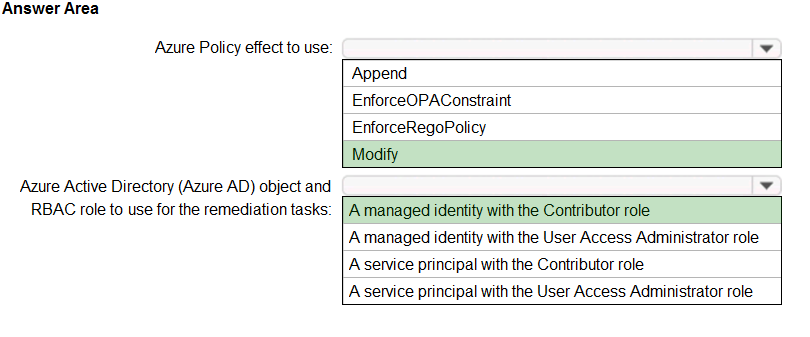

Box 1: Modify –
Modify is used to add, update, or remove properties or tags on a resource during creation or update. A common example is updating tags on resources such as costCenter. Existing non-compliant resources can be remediated with a remediation task. A single Modify rule can have any number of operations.
Incorrect Answers:
✑ The following effects are deprecated: EnforceOPAConstraint, EnforceRegoPolicy
✑ Append is used to add additional fields to the requested resource during creation or update. A common example is specifying allowed IPs for a storage resource.
Box 2: A managed identity with the Contributor role
✑ Managed identity
How remediation security works: When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity. Azure
Policy creates a managed identity for each assignment, but must have details about what roles to grant the managed identity.
✑ Contributor role
The Contributor role grants the required access to apply tags to any entity.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects https://docs.microsoft.com/en-us/azure/governance/policy/how-to/remediate-resources https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources
